Weaponizing Information
@FractalBounce: Jan 20, 2024

In the midst of the annual gathering of unelected oligarchs and state actors in the globalist-banker stronghold of Switzerland, a seemingly benign conference unfolds on the surface. Business leaders and government officials convene to address global challenges and seek solutions, presenting an image of collective goodwill. However, for those who perceive beyond the facade and recognize that the Kings of the Earth are guided by darker forces, this conference transforms into a coded display of a nefarious agenda (see Kings of the Earth: Rule by State-an). Drawing parallels to the deceptive nature of Satan masquerading as an angel of light, these rulers package their potentially malevolent plans in garments of goodness and righteousness. Professing love for the planet, commitment to truth, unity, and concerns for poverty and inequality, they unveil solutions under the guise of economic well-being and warnings about inflation. The critical question emerges: should we trust their words at face value? A closer examination reveals a sinister and perilous agenda, prompting a call to opposition from all who cherish freedom, irrespective of nationality or religion.
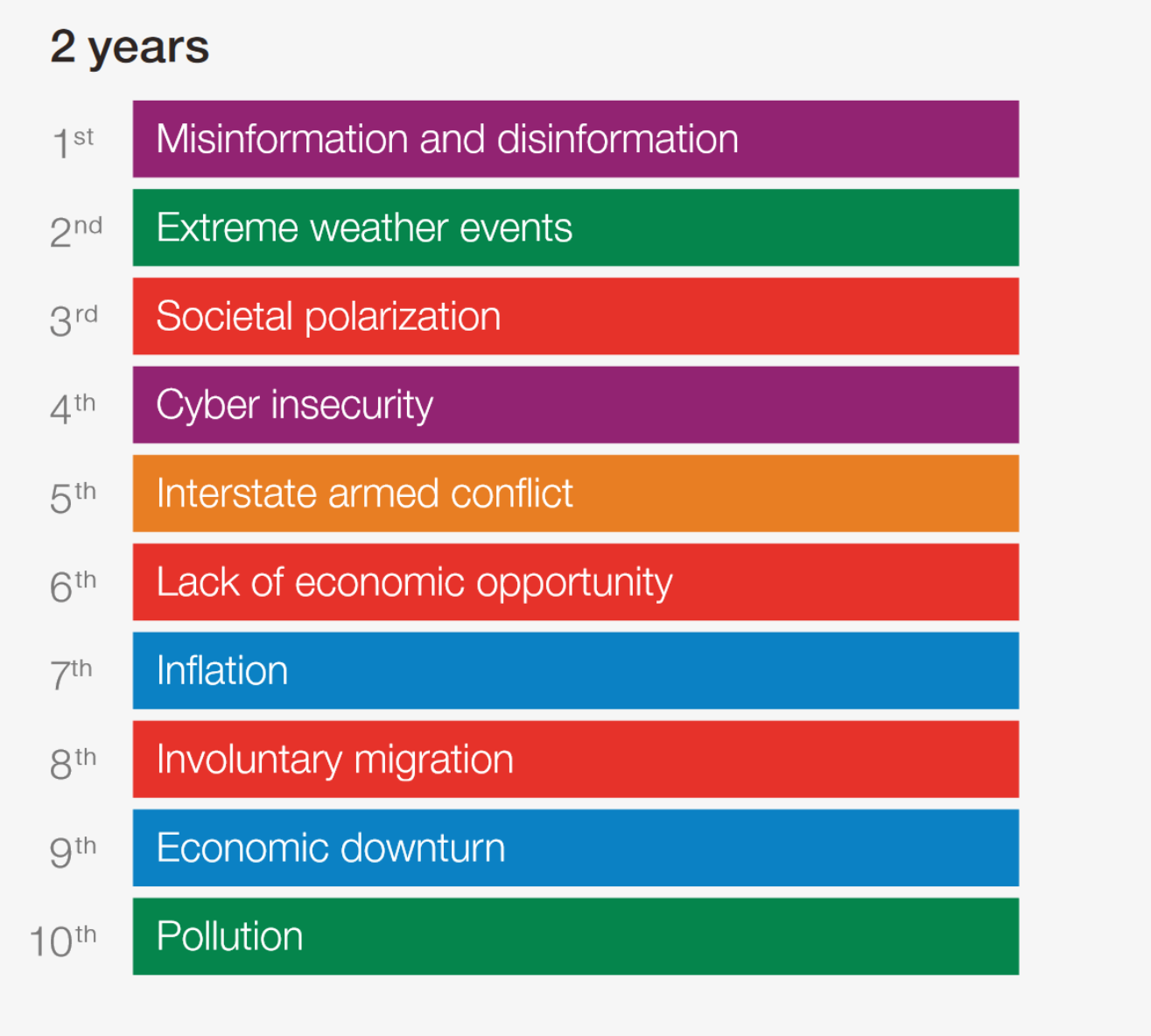
WEF top 10 global challenges for 2024
Above we see the top ten challenges for the upcoming years. Notice how they are color coded. Green of course is for environmental challenges, purple for tech, orange for social issues, blue for economic challenges and yellow for geopolitical problems. It is interesting to note the difference from last year’s top ten 2 year challenges to this years.

WEF top 10 global challenges for 2023
It’s worth noting that in the previous year, the cost-of-living crisis was singled out as the most pressing concern for the next two years. However, the 2024 report reveals that the cost-of-living issue did not even make it to the top 10. This paradoxical situation suggests that, despite worsening inflation and an escalating cost of living, it is not considered among the primary concerns according to the perspectives of influential figures and their experts. Additionally, disinformation, which was not a top 10 concern in the previous year, has now taken the lead position, surpassing even the pervasive threat of climate change. The landscape of priorities has also seen cyber security climb from the 8th position in the preceding year to the 4th spot in 2024, underscoring the growing significance of tech-related challenges when considering disinformation as the foremost issue. Notably, economic challenges, responsible for nearly 80% of the money supply printed post-COVID and contributing to the current inflationary trends, did not register in the top ten last year. These shifts emphasize the apparent fabrication of information, detached from reality, except for its role in reinforcing the anti-human narrative of the ruling class.
Let’s break down and decode the purple (misinformation and cyber threats) with the knowledge that Satan wraps his evil motives in righteousness.
Cyber Threats and Disinformation
At the forefront of concerns lies disinformation/misinformation, ranking as the primary apprehension. Its close association with cybersecurity, positioned at #4, suggests a perceived global challenge where individuals are becoming increasingly perplexed by the proliferation of falsehoods on the internet. However, applying the globalist decoder-ring reveals a narrative contrary to the publicized concern. Essentially, it implies that misinformation/disinformation, from their perspective, encompasses content that diverges from the State’s approved narrative. It denotes information challenging their agenda and narrative as a top priority to counter. Notably, the Obamas are spearheading efforts on behalf of the establishment in addressing this perceived threat, evident in every speech they’ve delivered over the past three years. Concealed within this narrative is the advocacy for ending internet anonymity, a crucial step in their plan to institute a digital ID system, akin to they control over the banking system. This entails the mandatory online identification of every individual through a state-issued ID. Figures like Eric Schmidt, former CEO of Google and CIA puppet, openly advocate for reporting individuals posting misinformation online to law enforcement, providing insight into the trajectory of these efforts. The overarching goal appears to be the eradication of digital privacy and anonymity, extending into the financial realm, where the shift towards predominantly digital transactions threatens the prospect of financial privacy.
So, what is their desired outcome, and how can they bring it to fruition? The answer is conspicuously evident, as they consistently unveil their plans, albeit requiring a globalist-decoder-ring for proper interpretation. Notably, concern #4, cybersecurity, absent from the 2023 list, becomes pivotal in comprehending their objectives. Through repeated warnings spanning years, intelligence reports have forecast a significant cyber incident slated to occur before 2025. This serves as a signal, indicating their intention to orchestrate a cyber incident, attribute it to Russia, and subsequently implement a cyber Patriot Act as the proposed solution. The anticipated resolution, however, comes at the cost of forfeiting both digital and financial privacy, replaced by pervasive surveillance measures.
In the book Countdown to Zero Day, Kim Zetter discusses how a cyberattack can have the destructive impact of a bombs. She points to the example of the hack on Iran’s nuclear reactors in which the world’s first digital weapon, called Stuxnet, was used. This virus was unlike anything seen before. Experts were perplexed by its complexity. Instead of gaining access to information on target computers like other worms, it escaped the cyber realm and caused physical destruction on a nuclear facility. Stuxnet is believed to have caused physical damage to Iran’s nuclear facilities, particularly the Natanz uranium enrichment plant. It exploited vulnerabilities in the control systems, causing disruptions to the centrifuges used for uranium enrichment. The worm is considered a sophisticated cyber weapon and is widely believed to be a joint creation of the United States and Israel, although neither country officially confirmed its involvement. Who else would be capable of creating such a weapon? The government’s ability to launch these types of attacks combined with their proclivity to use false flag attacks when the security state needs strengthening, creates a very scary scenario in which our domestic infrastructure is attacked and the blame is laid on a foreign actor.
What they Don’t Want Us to Know
Intelligence agencies and cyber threats
Cyber attacks were envisioned, developed and perfected by intelligence agencies. Most attacks are intelligence agencies penetrating to gain valuable intel or disrupt. In the book The Hacker and the State, Buchanan discusses how state actors, the driving force behind cyberattacks, are using cyberattacks to shape the world’s political landscape.
Hackers wiretap, spy, alter, sabotage, disrupt, attack, manipulate, interfere, expose, steal, and destabilize
Governments, through their respective intelligence agencies are at the forefront of developing cybersecurity toolkits. A hacker toolkit, also known as hacking software suite, refers to a collection of software tools, scripts, and resources that are commonly used by hackers or security professionals for various purposes, including penetration testing, vulnerability assessment, and, unfortunately, malicious activities.

What remains concealed from public awareness is the existence of a covert CIA cybersecurity toolkit named Umbrage, skillfully designed to execute false flag cyber attacks and attribute them to any chosen foreign entity. With this tool in hand, an assailant gains the capability to target a server, leaving behind a forensic trail meticulously crafted to point towards any preferred source. When law enforcement undertakes an investigation, the fabricated forensic trail invariably leads them to believe it originated from a foreign power. This intricate strategy empowers the orchestrators to fabricate a false flag incident, pin it on the Russians, and subsequently propose a solution, undoubtedly taking the shape of new restrictions and mandates. The role of Central Bank Digital Currencies (CBDC) in this scenario will be explored further in a subsequent post.

WikiLeaks’ Vault 7 is a trove of classified documents that was released in 2017, exposing the extensive hacking capabilities and cyber warfare tools of the Central Intelligence Agency (CIA). The leaks unveiled an array of sophisticated software tools used by the CIA for surveillance, cyber espionage, and remote manipulation of electronic devices, including smartphones and smart TVs. The significance of Vault 7 lies in its revelation of the agency’s global cyber arsenal, raising concerns about the erosion of privacy, abuse of power, and the blurred lines between national security and individual liberties. It sparked debates on the ethical implications of state-sponsored hacking, the need for stronger cybersecurity measures, and the delicate balance between intelligence agencies’ capabilities and citizens’ right to privacy.
In the leak, we learned about a covert CIA cybersecurity toolkit named Umbrage, skillfully designed to execute false flag cyber attacks and attribute them to any chosen foreign entity. With this tool in hand, an assailant gains the capability to target a server, leaving behind a forensic trail meticulously crafted to point towards any preferred source. When law enforcement undertakes an investigation, the fabricated forensic trail invariably leads them to believe it originated from a foreign power. This intricate strategy empowers the orchestrators to fabricate a false flag incident, pin it on the Russians, and subsequently propose a solution, undoubtedly taking the shape of new restrictions and mandates. The role of Central Bank Digital Currencies (CBDC) in this scenario will be explored further in a subsequent post.
The globalist death cult, having scrutinized the outcomes of the COVID experiment, recognized the challenges in enforcing physical constraints like curfews, mask mandates, and vaccine mandates. In a calculated move, they identified the internet as a more controllable realm and realized our profound dependence on it. Contemplating the potential impact of a global cyber event disrupting the internet, they strategized the introduction of a digital ID as the internet’s equivalent of a vaccine. Those desiring internet access would be compelled to comply with this digital identification, while dissenters rejecting it would be labeled as extremists, facing societal isolation. The cult envisions a scenario where the population, gathered in a digital prison, becomes easily manageable and devoid of dissent, creating their envisioned utopia.
In a wake-up call to all, the simultaneous emergence of global crises in the form of cyber threats demands heightened awareness. While advocating for global solutions, the alarming assertion that opposition to these measures equates to defiance against democracy and humanity should not be dismissed. The plea for suppressing dissent, irrespective of local laws, serves as a stark warning—a deceptive progression that demands our attention. It is time to recognize the calculated maneuvering of the ruling class, aimed at deceiving the masses to facilitate theft and secure compliance. This is a call for unyielding awareness, urging individuals to see through the veils of manipulation and safeguard their autonomy against a rising tide of global subjugation. It is time to wake up to the orchestrated deception and reclaim the rights that humanity was given by God.
Source
1Buchanan, Ben. The Hacker and the State: Cyber Attacks and the New Normal of Geopolitics (p. 7). Harvard University Press. Kindle Edition.